HNTB
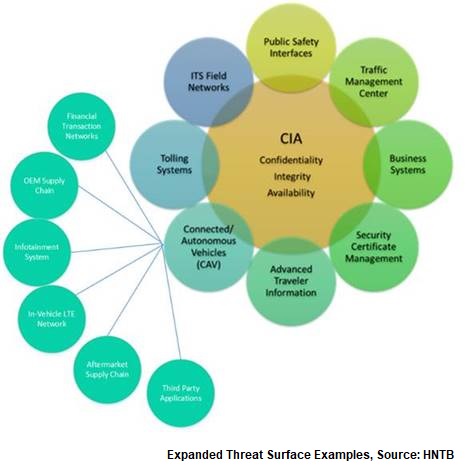
The implementation of connected vehicles has increased exponentially the possibility of unauthorized access to both ITS and IT networks. Agencies and related organizations that are deploying connected vehicle (CV) infrastructure face a multitude of new vulnerabilities. Here's HNTB's take on where those threats lie and how transportation agencies can begin addressing them.

CV safety applications may be our best hope of realizing "Vision Zero." But privately-owned vehicles are a virtual petri dish of vulnerable networks. Infotainment systems, telematics, Bluetooth, cellular networks and wireless sensor networks abound, and multiple computer processors are at work during any drive. There have already been numerous examples of hackers using their knowledge of these internal systems to gain access and control systems within the vehicle.
Since the vehicle has these vulnerabilities, connecting it to our transportation infrastructure systems means those vulnerabilities are introduced to our operational and information technology networks and we must include them in our risk analysis and protection plans.
The traffic cabinet … has become one of the weakest points for ITS security
Because it is the first access point in the field, one of the most significant threats comes through the traffic cabinet, the hub for ITS and traffic signal data. By compromising a CV device, hackers can potentially launch attacks against other networks via this entry point. A hacker could also send "trusted" messages to other vehicles and infrastructure.
The traffic cabinet can no longer be protected by a lock and camera. It has become one of the weakest points for ITS security due to the abundance and diversity of communication interfaces converging within it.
The Internet of Things (IoT) and CV — Protecting Critical Infrastructure
In an April 2018 presentation to the Wall Street Journal CEO Council Conference, Nicole Eagan, the CEO of Darktrace, reported that hackers had breached the automated thermostat of a casino aquarium and, through it, had gained access to the high roller database. This sort of malicious intrusion is more common than most people think. According to a study by Aruba Networks involving more than 3,000 companies, 84 percent of them had experienced some type of IoT breach.
In the past, cybersecurity training focused on social engineering and user profiles, instructing users how to avoid clicking on nefarious links. As the IoT applications take off, this kind of training addresses only about 20 percent of threats because there's so much decision-making taking place at the machine level (edge computing). The connected home is a great example. Your dishwasher or refrigerator could be sharing the same network where you pay your bills!
Now, let's translate that to the transportation world. IoT devices in cars and traffic cabinets mean transportation agencies have to implement security by design — not as an afterthought. They need to start bringing security experts in as part of their initial design concept team.
Unintentional Impacts to Availability
Security concepts are built around the "big three" security triad of confidentiality, integrity and availability. Availability means the data is accessible and usable when needed. Communications interference often restricts availability, but interference in ITS data communications doesn't always result from intentional hacks.
Recent CV deployments using dedicated short-range communications (DSRC) channels also have illustrated potential unintended barriers to effective data transmission. During one local deployment, CV applications worked in the test environment but failed in the field. We tracked the interference to a HAM radio operator. FCC rules allow HAM licensees to use DSRC channels for public good, which in this case was providing connectivity for 9-1-1 service during a cable cut. However, that use is secondary and they must not interfere with CV applications.
We worked for over a year with assistance from the State DOT, U.S. DOT and the Federal Communications Commission to get a final cease and desist. Many large urban areas are using similar technology, and agencies will need to deal with each type of interference separately, issuing cease and desist notices with proper proof of interference.
We also have learned that we need to conduct a full spectral analysis before deploying CV technology. On another project, we encountered unexpected interference from drones in the field. Although the drones themselves operate on a low-frequency control spectrum, they were streaming video back on the 5.8 spectrum, which butts up against DSRC and creates localized interference.
Another project shared that their apps were being interfered with by individuals using GPS jammers so their boss wouldn't know where they were having lunch in the company truck.




